Others
Research Experiences
APA AUT CERT (https://apa.aut.ac.ir/en):
- Research Assistant at AUT CERT Lab. - (June 2021 - Now )
"Web & Mobile Application Security Analysis" with Professor Babak Sadeghiyan
In this lab, we analyze the security vulnerabilities of web and mobile applications with static and dynamic oriented and we provide awareness to business owners of the existence of security bugs that we have identified based on the OWASP standard and for improve and fix these vulnerabilities give them advice.
Amirkabir University of Technology (Tehran Polytechnic) (AUT):
- Research Assistant at Security Analysis Lab. - (Sep. 2021 - Now )
"A Method for Protecting Privacy of IoT Healthcare Data Against Machine Learning Attack" M.Sc. thesis with Professor Hamid Reza Shahriari
Machine learning models leak information about the individual data records on which they were trained. Reza Shokri et al.[1] focus on the basic membership inference attack: given a data record and black-box access to a model, determine if the record was in the model's training dataset. To perform membership inference against a target model, they make adversarial use of machine learning and train their own inference model to recognize differences in the target model's predictions on the inputs that it trained on versus the inputs that it did not train on. They empirically evaluate their inference techniques on classification models trained by commercial "machine learning as a service" providers such as Google and Amazon. Using realistic datasets and classification tasks, including a hospital discharge dataset whose membership is sensitive from the privacy perspective, they show that these models can be vulnerable to membership inference attacks. So, in this lab, we are looking to find a way to protect healthcare data privacy in IoT which causes the data to be stored anonymously and enter the training stage of machine learning algorithms so that these machine learning algorithms do not understand the original data. Also, this solution must be lightweight for IoT environment.
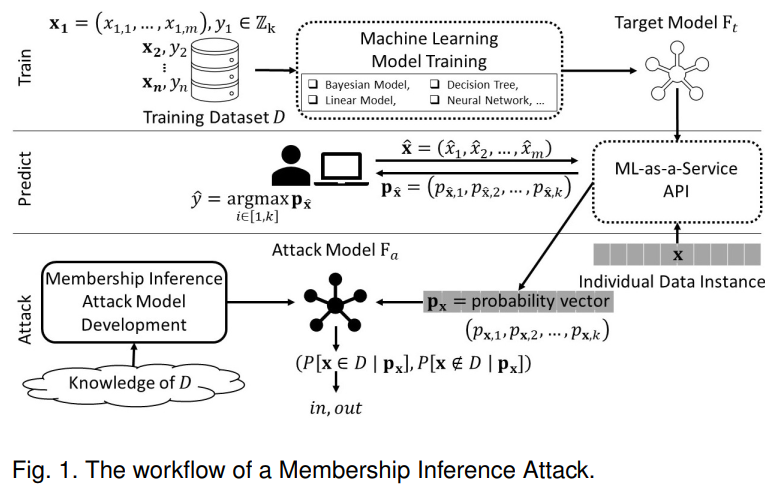
Picture Reference = [2]
Technical Reports
Amirkabir University of Technology (Tehran Polytechnic) (AUT):
- Project Report for Applied Cryptography (Graduate Course), (+Oral Presentation) [In Persian] - ( Oct. 2020 - Feb. 2021)
"Design and Implementation a New Cryptography Algorithm" with Professor Babak Sadeghiyan
Designing a cryptographic algorithm can be one of the solutions in order to evaluate the level of knowledge of an active expert in the field of applied cryptography. In this project, we have designed a new algorithm using different parts of several encryption algorithms. In this project, the input of the algorithm is a 96-bit fragment. The structure used to do this project is a Feistel type 1 structure. After entering the parts into the algorithm, a part of it is affected by the function f and then it is XORed with the other part. Finally, the first round ends with the moving of the parts. This is done for twelve consecutive rounds. The f function used in this project is designed similarly to the Blowfish function. Also, another part of this project is related to the key part, where 96 bits of the main key are entered into the system. By applying the function on this key, a total of 36 subkeys are produced, which are used in 12 rounds. The function applied to the key is similar to the structure of the AES key function with a slight modification. Finally, this algorithm is implemented in OFB mode (both encryption and decryption), and avalanche, integrity, and NIST tests are performed on it. In addition, the number of lines of this algorithm is 344 lines in Python along with the codes related to the Avalanche test and completeness and OFB mode. This number of lines is defined without considering the codes related to NIST tests and tables.
Overview:
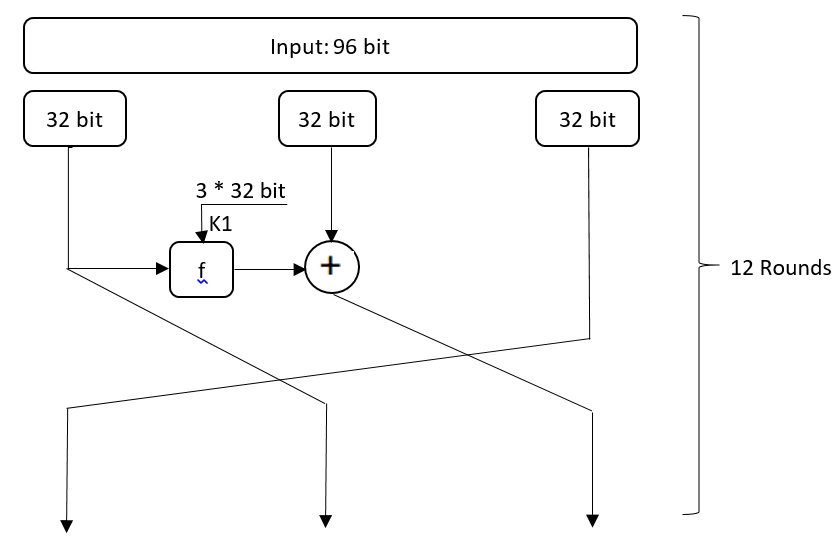
More details and code: New Cryptography Algorithm

